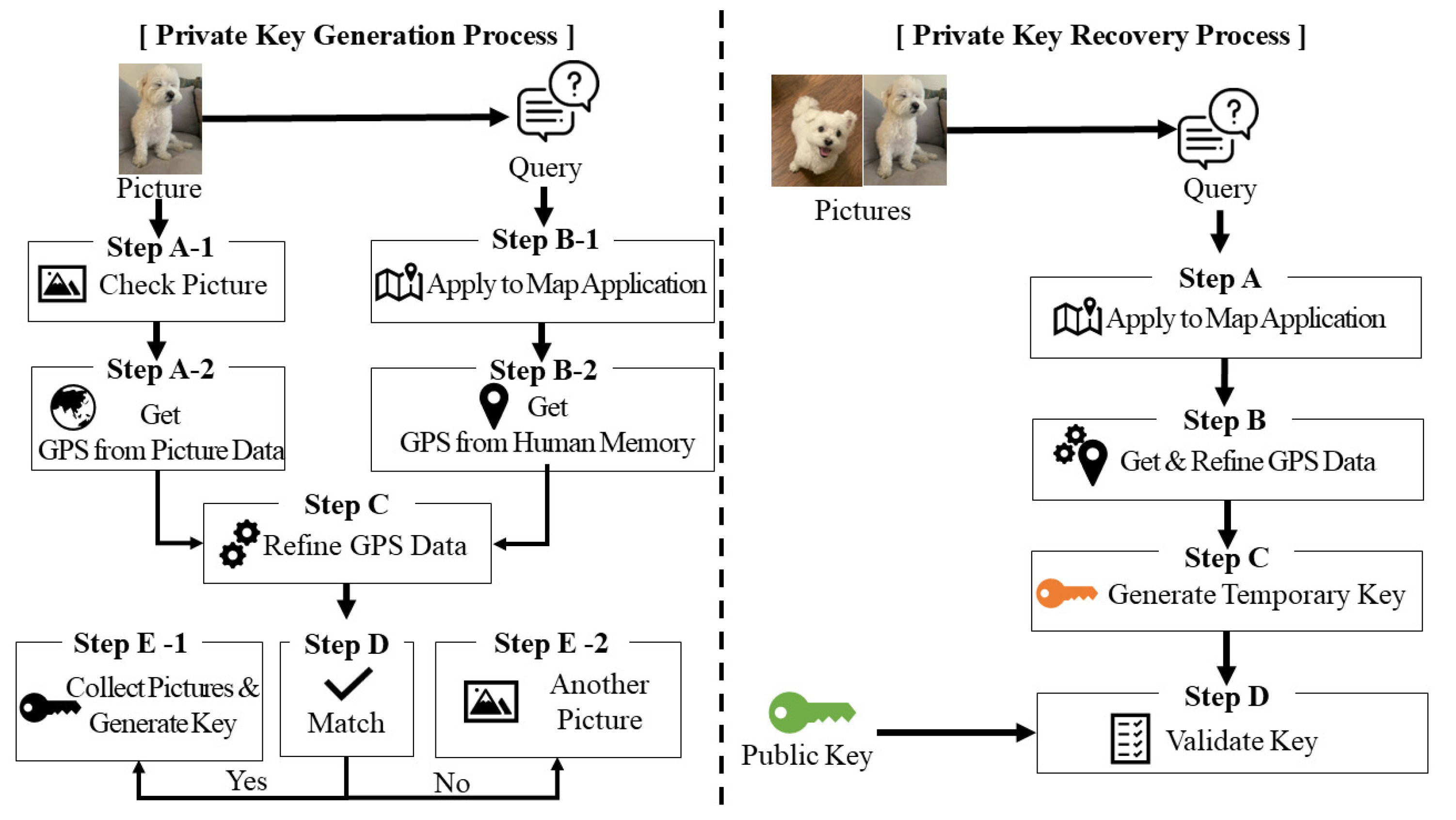
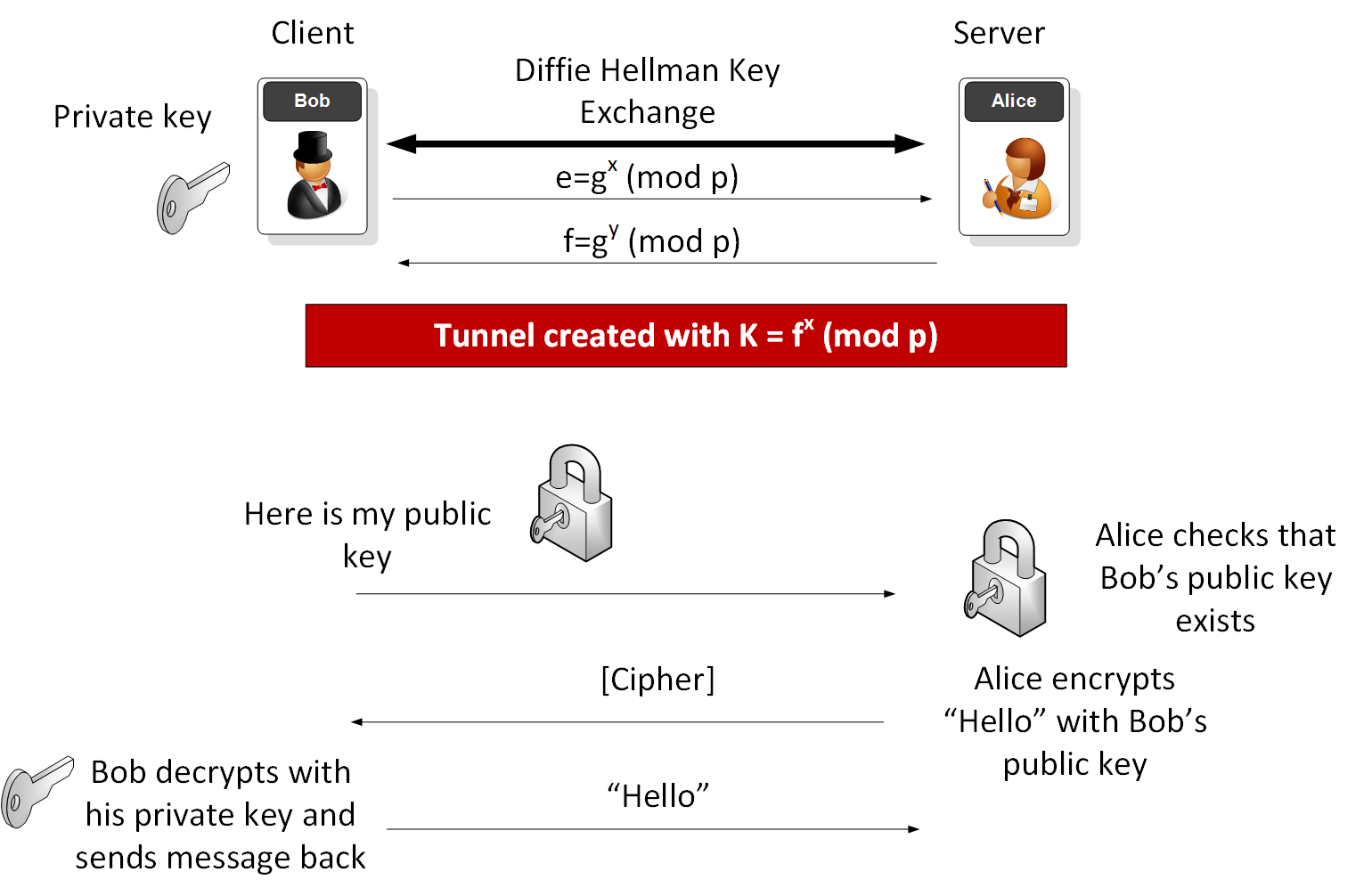
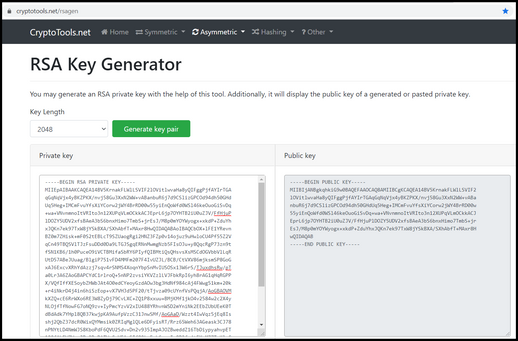
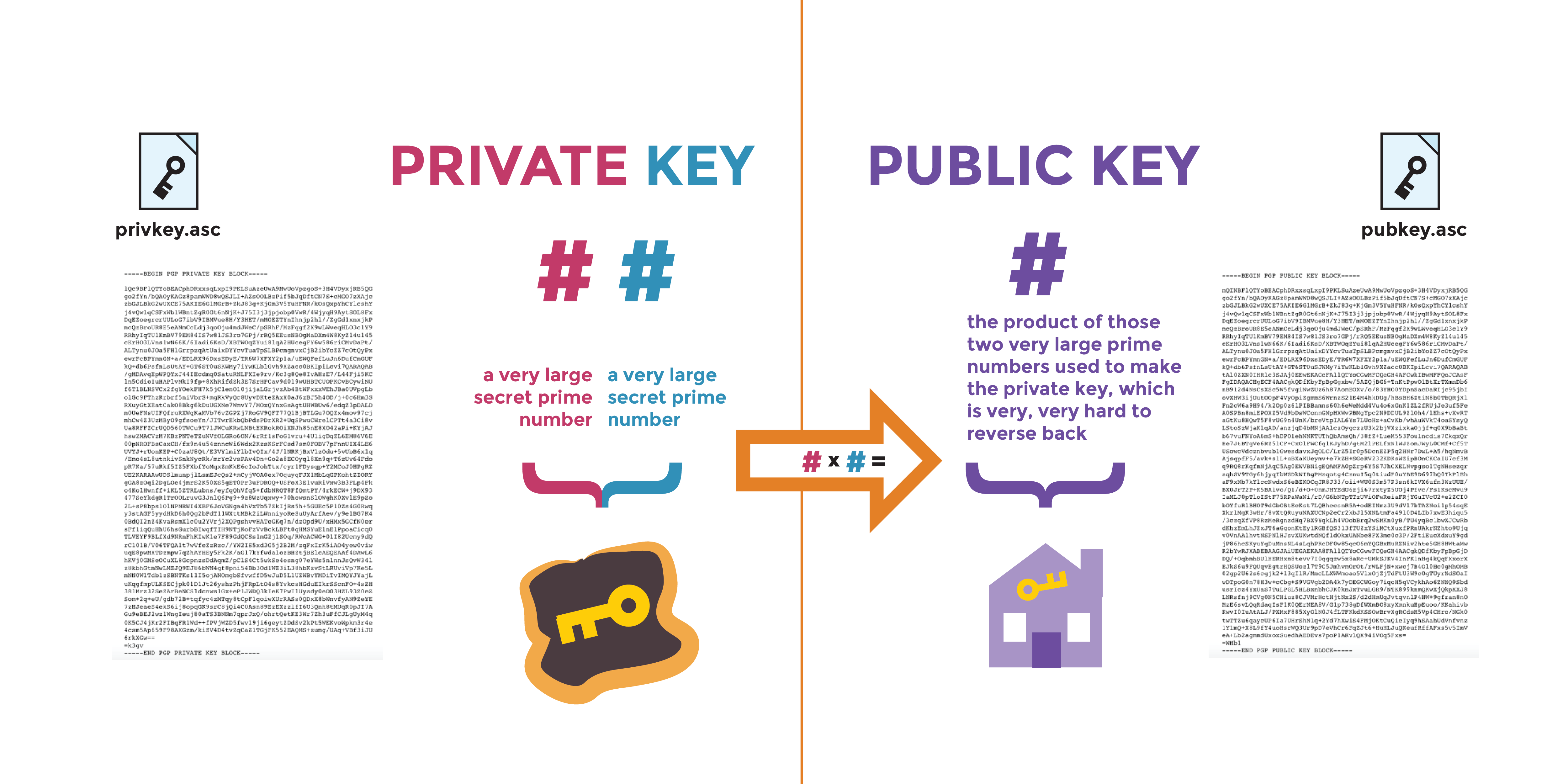
Example of public-private key generation for LWE based cryptography.... | Download Scientific Diagram
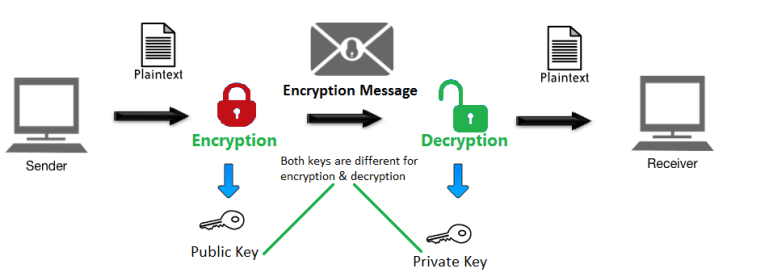
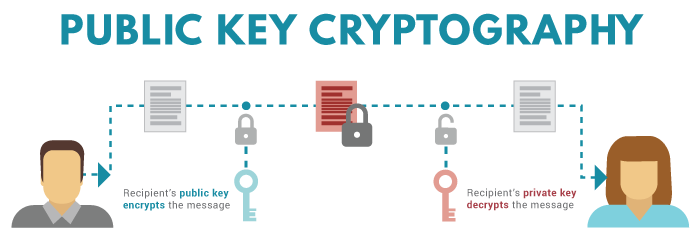
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense

5c) Using RSA key generation scheme with p=11, q=5, e=3, find the public key & private key pair - YouTube
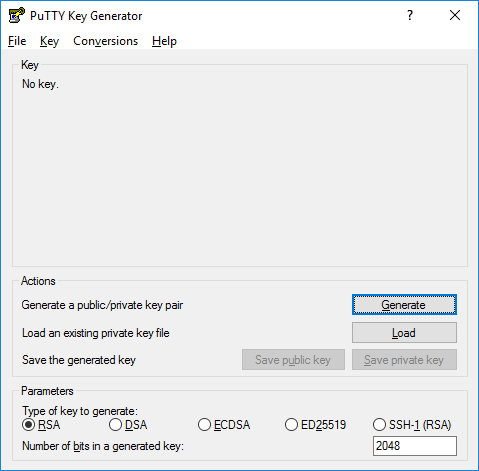
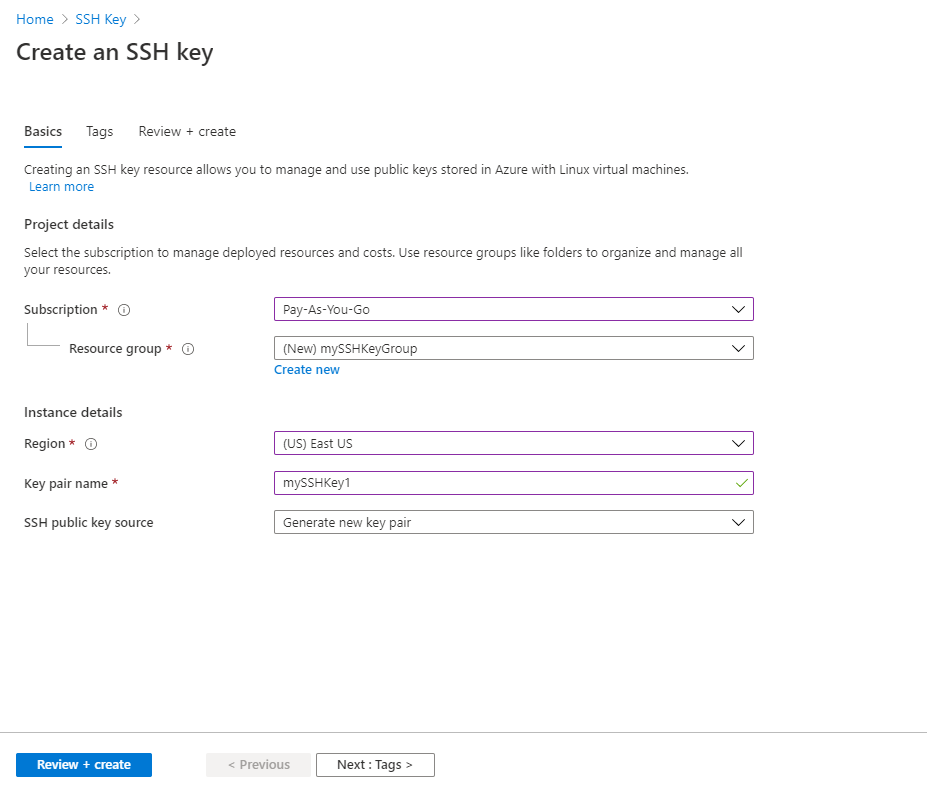
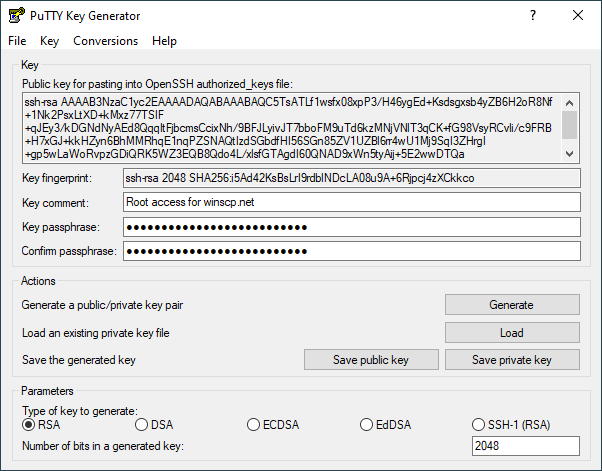
How to install and use puttygen to create new key pairs and change passphrases. Installing keys on server, managing SSH keys.