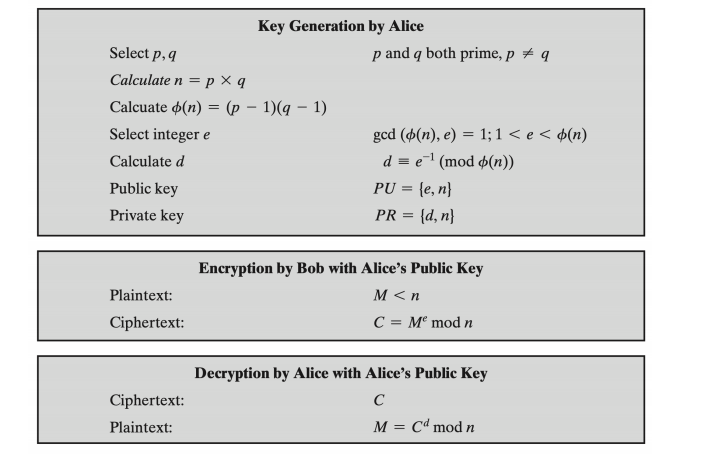
An Effective and enhanced RSA based Public Key Encryption Scheme (XRSA) | International Journal of Information Technology
![PDF] Efficient RSA Key Generation Protocol in a Two-Party Setting and its Application into the Secure Multiparty Computation Environment | Semantic Scholar PDF] Efficient RSA Key Generation Protocol in a Two-Party Setting and its Application into the Secure Multiparty Computation Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3814d0ffa05d6c3afff2d829675b7be549b4cf40/11-Table3.2-1.png)
PDF] Efficient RSA Key Generation Protocol in a Two-Party Setting and its Application into the Secure Multiparty Computation Environment | Semantic Scholar
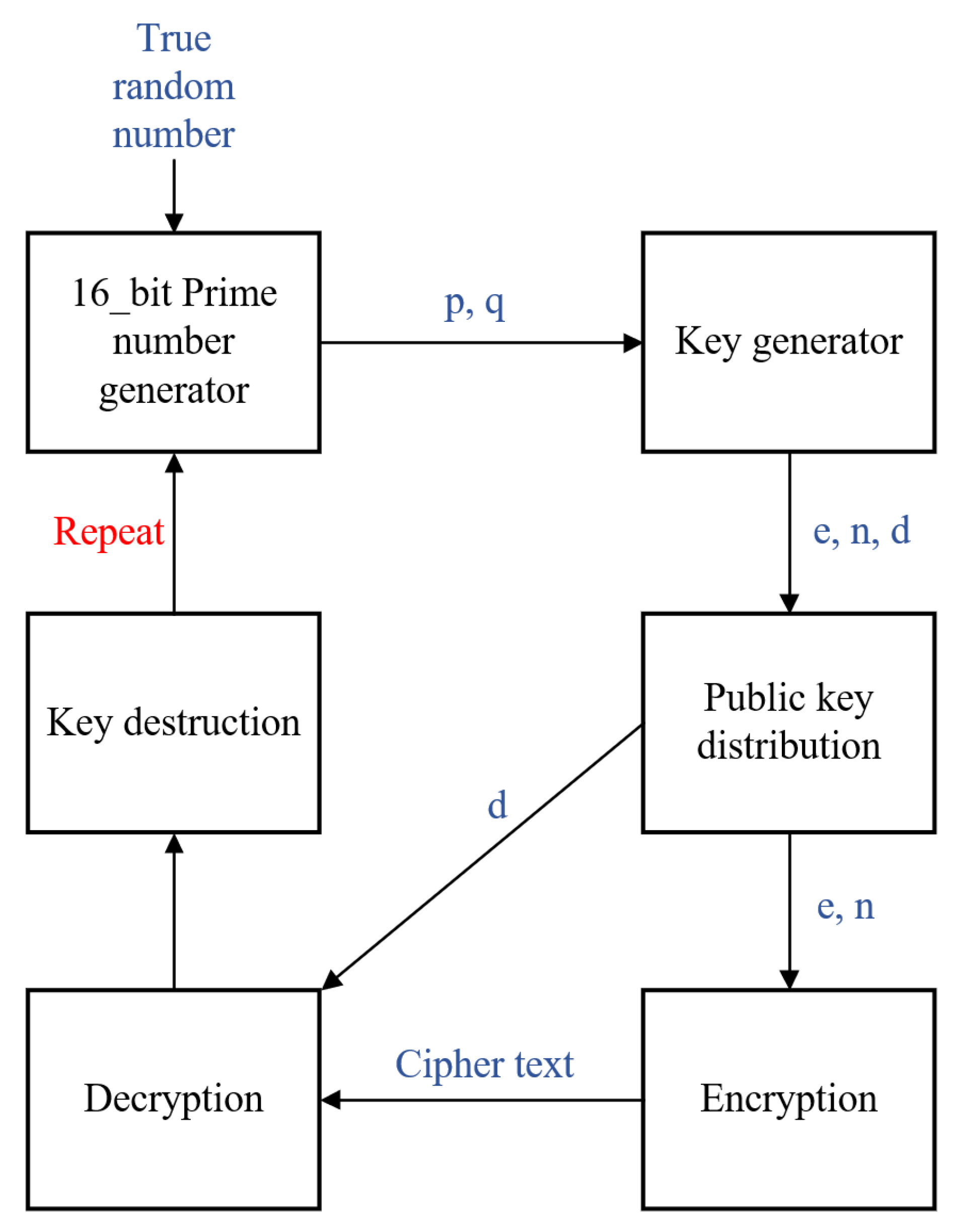
Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices
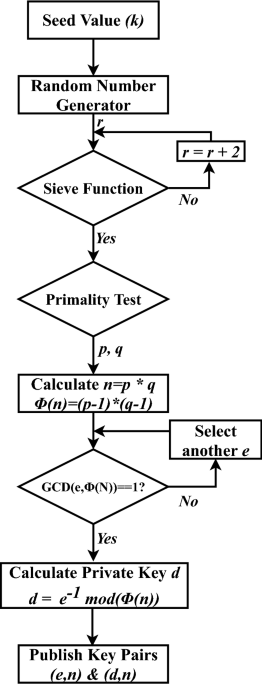

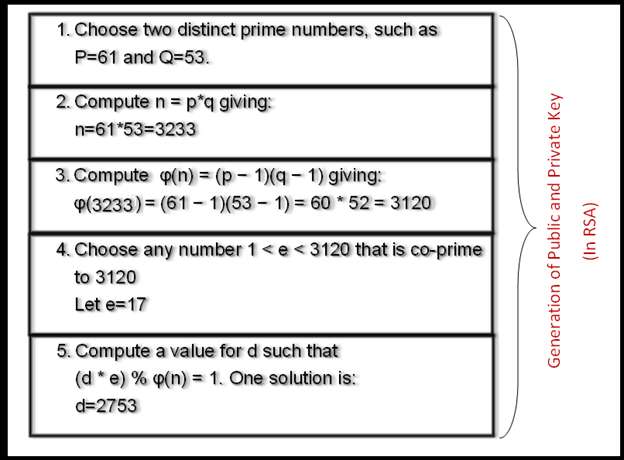


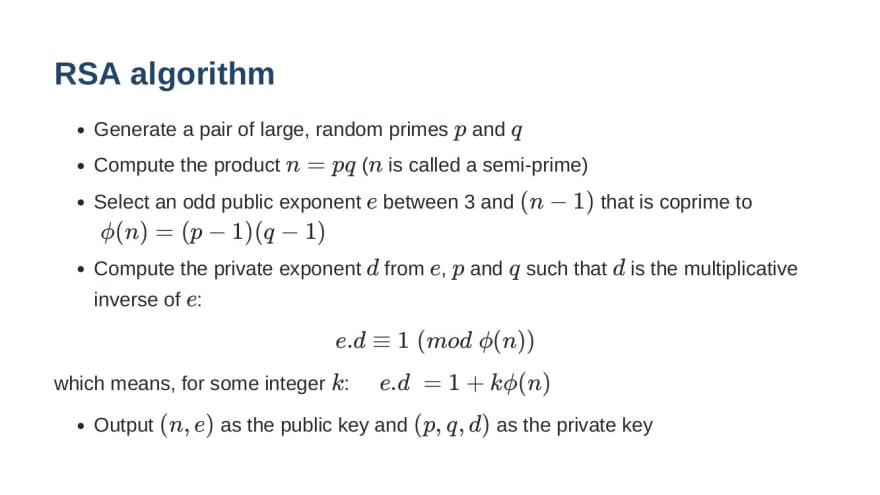

![RSA algorithm[8, 14] | Download Scientific Diagram RSA algorithm[8, 14] | Download Scientific Diagram](https://www.researchgate.net/publication/280246343/figure/fig5/AS:391598006390788@1470375648736/RSA-algorithm8-14.png)