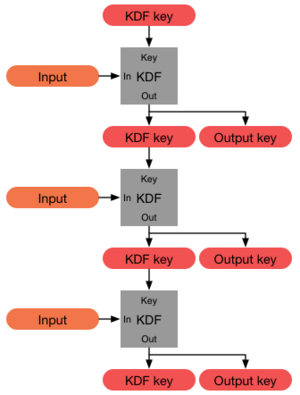
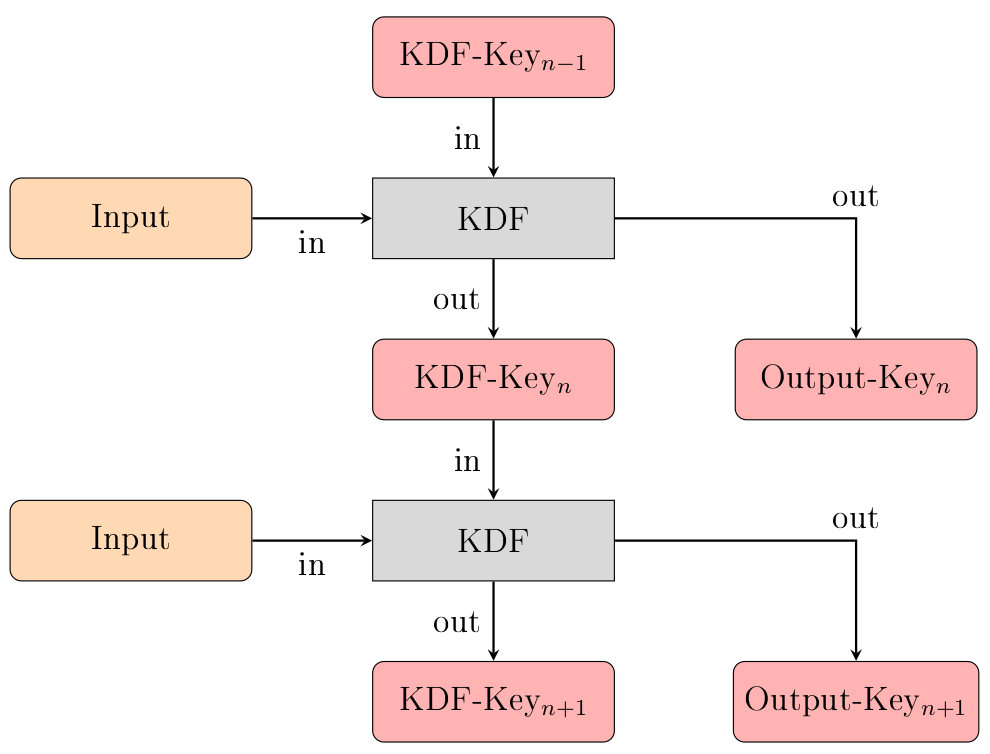
key derivation - Is a PBKDF2-derived master key easier cracked if very many Data Protection Keys are derived from it? - Cryptography Stack Exchange

1 Standardizing Key Derivation Functions Hugo Krawczyk IBM Research Or: google kdf hmac. - ppt download

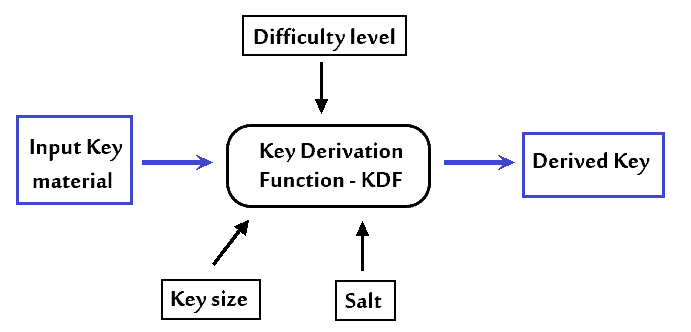
Password Stretching using Key Derivation Function(KDF) | by Sodimu Segun Michael | HackerNoon.com | Medium



![Key derivation - Practical Internet of Things Security - Second Edition [Book] Key derivation - Practical Internet of Things Security - Second Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781788625821/files/assets/7e4474a1-658a-4b60-a90d-41fc615bd89e.png)

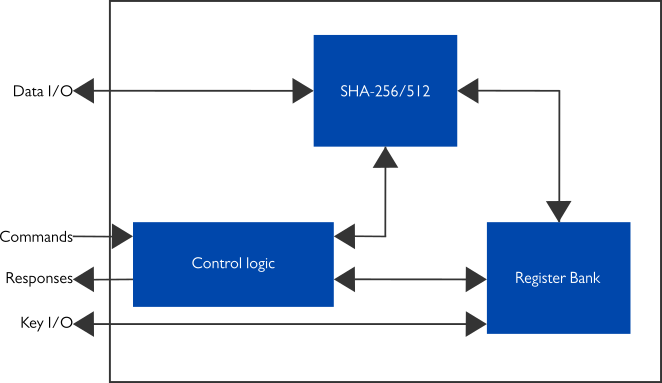

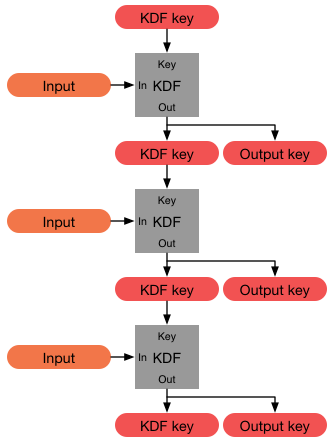

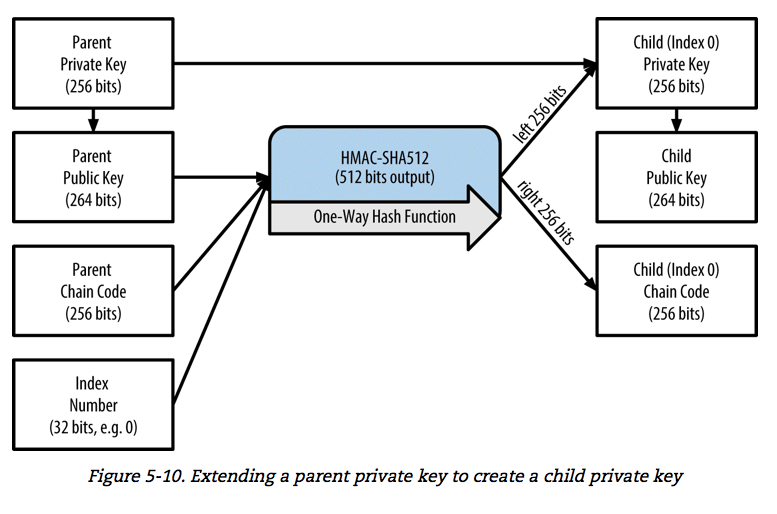
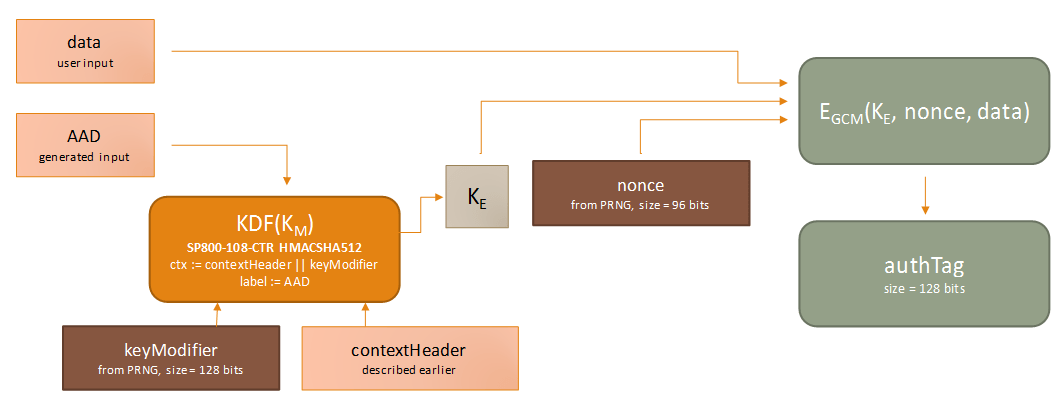


![PDF] Key derivation function based on stream ciphers | Semantic Scholar PDF] Key derivation function based on stream ciphers | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5550d34ebdd20472dab7708f293ddd91ffe06bcb/42-Figure2.2-1.png)